Messages like "You have a Virus in your software" are received into my Inbox on daily basis, and a lots of them comes from AVG Antivirus. So I decided to check the current status of AVG false positives, by scanning the utilities folder of my site.
First, I copied the utils folder of my site into a new place (I don't really want that AVG will touch my original site folder...), and then I allowed AVG Antivirus to scan the folder.
After AVG finished the scan, it splited the scan result into 2 categories: Infections and Spyware.
Most of the alerts on my utilities folder appeared under the 'Spyware' section.
I really would want to understand what is going in the minds of AVG guys when they decided to detect my software as Spyware.
Anyway, I used my own
SysExporter utility to grab the scan result from AVG and display it as HTML. Luckily,
SysExporter is not detected as infection by AVG, otherwise, it wouldn't allow me to run and use it.
So here's the AVG "False Positive" list, the Spyware section:
| C:\Utils\asterie.zip | Potentially harmful program HackTool.DOI
|
| C:\Utils\asterie.zip:\asterie.exe | Potentially harmful program HackTool.DOI
|
| C:\Utils\netpass.zip | Potentially harmful program HackTool.FAJ
|
| C:\Utils\netpass.zip:\netpass.exe | Potentially harmful program HackTool.FAJ
|
| C:\Utils\netpass_setup.exe | Potentially harmful program HackTool.FAJ
|
| C:\Utils\netpass_setup.exe:\netpass.exe | Potentially harmful program HackTool.FAJ
|
| C:\Utils\netpass_setup.exe:\ziz1384.tmp:\netpass.exe | Potentially harmful program HackTool.FAJ
|
| C:\Utils\pspv.zip | Potentially harmful program HackTool.CBX
|
| C:\Utils\pspv.zip:\pspv.exe | Potentially harmful program HackTool.CBX
|
| C:\Utils\sniffpass.zip | Potentially harmful program HackTool.FMT
|
| C:\Utils\sniffpass.zip:\SniffPass.exe | Potentially harmful program HackTool.FMT
|
| C:\Utils\sniffpass_setup.exe | Potentially harmful program HackTool.FMT
|
| C:\Utils\sniffpass_setup.exe:\SniffPass.exe | Potentially harmful program HackTool.FMT
|
| C:\Utils\sniffpass_setup.exe:\ziz1384.tmp:\SniffPass.exe | Potentially harmful program HackTool.FMT
|
| C:\Utils\vncpassview.zip | Potentially harmful program HackTool.EEI
|
| C:\Utils\vncpassview.zip:\VNCPassView.exe | Potentially harmful program HackTool.EEI
|
And this one is the Infections section:
| C:\Utils\lsasecretsdump.zip | Trojan horse Generic10.SZR
|
| C:\Utils\lsasecretsdump.zip:\LSASecretsDump.exe | Trojan horse Generic10.SZR
|
And finally, here's another issue with AVG and other Antivirus software:
When you exit from the Antivirus software, it won't display any Virus/Trojan/Spyware warning, but the service of the Antivirus is still running in the background, and prohibits you from running any file that is detected as infected.
This mean that if you try to run one of my tools that are detected as Spyware/Virus while AVG application is not running, you'll get the following error message:
"Windows cannot access the specified device, path, or file. You may not have the appropriate permission to access the item".
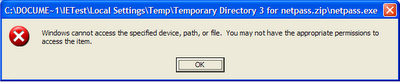
Most people that get this kind of error, think that there is a bug in my software, and don't know that the Antivirus is the one that cause the problem.